Samba 4 is the ambitious next version of the Samba suite that is being developed in parallel to the stable 3.0 series. The main emphasis in this branch is support for the Active Directory logon protocols used by Windows 2000 and above.
Samba 4 is currently not yet in a state where it is usable in production environments
The source code can be Download Now
Tuesday, August 12, 2008
FreeBSD with Active Directory Single Sing On
Introduction
This document describes how to join a FreeBSD box to a Windows domain controller and to control access to the FreeBSD box. We will be using Samba’s WinBind and Kerberos for authentication.
This document assumes that you have a functioning FreeBSD sever on a network with internet access.
Install Samba Port
1. Log into FreeBSD Sever
2. Su to root “su –“
3. Change to Samba 3 ports directory “cd /usr/ports/net/samba3”
4. Compile and install Samba 3 “make install”
a. Select ONLY the following Samba options in the configuration “LDAP, ADS, WINBIND, ACL_SUPPORT, SYSLOG, UTMP, PAM_SMBPASS, EXP_MODULES, & POPT”
Configure Samba
1. To get Samba and Winbind to work on boot up add the following to /etc/rc.conf file:
nmbd_enable=”YES”
smbd_enable=”YES”
winbindd_enable=”YES”
kerberos5_server_enable=”YES”
kadmind5_server_enable=”YES”
2. Move the orginal smb.conf file “mv /usr/local/etc/smb.conf /usr/local/etc/smb.conf.default”
3. Copy the following to smb.conf…
[global]
workgroup = YOURDOMAIN
server string = FreeBSD Server %v
load printers = no
encrypt passwords = yes
socket options = TCP_NODELAY SO_RCVBUF=8192 SO_SNDBUF=8192
dns proxy = no
smb ports = 139
security = ADS
realm = YOURDOMAIN.COM
password server = domaincontroler1.yourdomain.com
password server = domaincontroler2.yourdomain.com
winbind separator = \
idmap uid = 10000-20000
idmap gid = 10000-20000
winbind enum users = yes
winbind enum groups = yes
template homedir = /home/%D/%U
template shell = /bin/tcsh
client ntlmv2 auth = yes
winbind use default domain = yes
restrict anonymous = 2
domain master = no
local master = no
preferred master = no
disable netbios = no
dos charset = ASCII
unix charset = UTF8
display charset = UTF8
Configure Kerberos
1. Edit /etc/krb5.conf (it probably doesn’t exist) and add the following text:
[logging]
default = SYSLOG:INFO:LOCAL7
[libdefaults]
ticket_lifetime = 24000
clock_skew = 300
default_realm = YOURDOMAIN.COM
[realms]
domain.LOCAL = {
kdc = domaincontroler1.yourdomain.com:88
kdc = domaincontroler2.yourdomain.com:88
admin_server = domaincontroler1.yourdomain.com:464
admin_server = domaincontroler2.yourdomain.com:464
default_domain = yourdomain.com
}
[domain_realm]
.domain.local = YOURDOMAIN.COM
domain.local = YOURDOMAIN.COM
2. Test Kerberos by typing “kinit”. Put a username that is on the domain controller. You should get a response of “kinit: NOTICE: ticket renewable lifetime is 1 week” and you will know its working. You can also do a “klist” to see who issued the ticket and verify its from the Smartech domain.
Joining The Domain
1. We should now be able to join the domain, enter the following:
/usr/local/bin/net ads join -U domaincontroler1.yourdomain.com -U administrator
2. It will prompt you for the domain controllers administrator password. If your successful you should see a reply like:
Using short domain name — YOURDOMAIN
Joined ‘FBTEST2′ to realm ‘YOURDOMAIN.COM’
Turning Samba on and Testing
1. Run “/usr/local/etc/rc.d/samba start”
2. Your output should look like this:
Removing stale Samba tdb files: done
Starting nmbd.
Starting smbd.
Starting winbindd.
3. Then run “wbinfo -u” and it should list all of the domain users.
4. Also “wbinfo -g” will show you a list all of the domain groups.
Name Switch Service
1. Now we tell pam to authenticate from the AD server first then failover to local accounts if the domain controller is over.
2. Edit the “/etc/nsswitch” file. Make it match the following example. Notice we only make changes to the group and passwd entries.
group: winbind files
group_compat: nis
hosts: files dns
networks: files
passwd: winbind files
passwd_compat: nis
shells: files
services: compat
services_compat: nis
protocols: files
rpc: files
Automatic Creation of Home Directories
1. To make automatic home directories we need to compile and install pam_mkhomedir port.
cd /usr/ports/security/pam_mkhomedir
make install
mkdir /home/YOURDOMAIN.COM
Setup SSHD Authentication with PAM
1. Now we have to make SSHD authenticate with PAM and WinBind by editing “/etc/pam.d/sshd”. This will also do the automatic home directory creation.
2. Add “auth sufficient /usr/local/lib/pam_winbind.so # Allows access to everyone in the domain” to the 3rd line under “# auth”
3. Add “session required /usr/local/lib/pam_mkhomedir.so” to the 2nd line under “# session # Creates home directories for AD authenticated users.”
4. You can also run “getent passwd” and “getent group” to get the list of users and groups that combine both the domain controllers user list with the local list and the same for groups.
Testing Domain Authentication
1. Try logging into the account with an account on the domain controller and its password. Once logged in make sure the account has a home directory by typing “pwd” to see your current path.
Setup AD Group Access Restrictions
1. Now we need to restrict the FreeBSD box to particular users. We do not want everyone to have access. No now we will need to gather some needed information.
a. Run “wbinfo -g” to view all of the groups that are in the domain controller or look in the Active Directory Users and Computers.
b. Note the groups you want to have access to the box. You are required to add “Domain Admins” as a group to all FreeBSD boxes.
c. Next we need the SID of each of the groups.
i. wbinfo -n “GROUPNAME” , will return the SID of the group.
fbtest2# wbinfo -n “domain admins”
S-1-5-21-1328793019-4053271937-1264903302-512 Domain Group (2)
ii. The long number starting with S is the SID, i.e. S-1-5-21-1328793019-4053271937-1264903302-512
2. Now we need to add the SID’s to /etc/pam.d/sshd to allow those users access and to remove access for everyone.
a. Comment out “auth sufficient /usr/local/lib/pam_winbind.so # Allows access to everyone in the domain”
b. Add “auth sufficient /usr/local/lib/pam_winbind.so try_first_pass require_membership_of= # Group: ” below it.
i.e. “auth sufficient /usr/local/lib/pam_winbind.so try_first_pass require_membership_of=S-1-5-21-1328793019-4053271937-1264903302-512 # Group: Domain Admins”
c. Make sure you label the “GROUP NAME” so that we know which group the SID belongs to.
d. Add the rest of the groups you want to have access to the box.
3. Add a user to a group on the domain controller and test your loggin.
This document describes how to join a FreeBSD box to a Windows domain controller and to control access to the FreeBSD box. We will be using Samba’s WinBind and Kerberos for authentication.
This document assumes that you have a functioning FreeBSD sever on a network with internet access.
Install Samba Port
1. Log into FreeBSD Sever
2. Su to root “su –“
3. Change to Samba 3 ports directory “cd /usr/ports/net/samba3”
4. Compile and install Samba 3 “make install”
a. Select ONLY the following Samba options in the configuration “LDAP, ADS, WINBIND, ACL_SUPPORT, SYSLOG, UTMP, PAM_SMBPASS, EXP_MODULES, & POPT”
Configure Samba
1. To get Samba and Winbind to work on boot up add the following to /etc/rc.conf file:
nmbd_enable=”YES”
smbd_enable=”YES”
winbindd_enable=”YES”
kerberos5_server_enable=”YES”
kadmind5_server_enable=”YES”
2. Move the orginal smb.conf file “mv /usr/local/etc/smb.conf /usr/local/etc/smb.conf.default”
3. Copy the following to smb.conf…
[global]
workgroup = YOURDOMAIN
server string = FreeBSD Server %v
load printers = no
encrypt passwords = yes
socket options = TCP_NODELAY SO_RCVBUF=8192 SO_SNDBUF=8192
dns proxy = no
smb ports = 139
security = ADS
realm = YOURDOMAIN.COM
password server = domaincontroler1.yourdomain.com
password server = domaincontroler2.yourdomain.com
winbind separator = \
idmap uid = 10000-20000
idmap gid = 10000-20000
winbind enum users = yes
winbind enum groups = yes
template homedir = /home/%D/%U
template shell = /bin/tcsh
client ntlmv2 auth = yes
winbind use default domain = yes
restrict anonymous = 2
domain master = no
local master = no
preferred master = no
disable netbios = no
dos charset = ASCII
unix charset = UTF8
display charset = UTF8
Configure Kerberos
1. Edit /etc/krb5.conf (it probably doesn’t exist) and add the following text:
[logging]
default = SYSLOG:INFO:LOCAL7
[libdefaults]
ticket_lifetime = 24000
clock_skew = 300
default_realm = YOURDOMAIN.COM
[realms]
domain.LOCAL = {
kdc = domaincontroler1.yourdomain.com:88
kdc = domaincontroler2.yourdomain.com:88
admin_server = domaincontroler1.yourdomain.com:464
admin_server = domaincontroler2.yourdomain.com:464
default_domain = yourdomain.com
}
[domain_realm]
.domain.local = YOURDOMAIN.COM
domain.local = YOURDOMAIN.COM
2. Test Kerberos by typing “kinit
Joining The Domain
1. We should now be able to join the domain, enter the following:
/usr/local/bin/net ads join -U domaincontroler1.yourdomain.com -U administrator
2. It will prompt you for the domain controllers administrator password. If your successful you should see a reply like:
Using short domain name — YOURDOMAIN
Joined ‘FBTEST2′ to realm ‘YOURDOMAIN.COM’
Turning Samba on and Testing
1. Run “/usr/local/etc/rc.d/samba start”
2. Your output should look like this:
Removing stale Samba tdb files: done
Starting nmbd.
Starting smbd.
Starting winbindd.
3. Then run “wbinfo -u” and it should list all of the domain users.
4. Also “wbinfo -g” will show you a list all of the domain groups.
Name Switch Service
1. Now we tell pam to authenticate from the AD server first then failover to local accounts if the domain controller is over.
2. Edit the “/etc/nsswitch” file. Make it match the following example. Notice we only make changes to the group and passwd entries.
group: winbind files
group_compat: nis
hosts: files dns
networks: files
passwd: winbind files
passwd_compat: nis
shells: files
services: compat
services_compat: nis
protocols: files
rpc: files
Automatic Creation of Home Directories
1. To make automatic home directories we need to compile and install pam_mkhomedir port.
cd /usr/ports/security/pam_mkhomedir
make install
mkdir /home/YOURDOMAIN.COM
Setup SSHD Authentication with PAM
1. Now we have to make SSHD authenticate with PAM and WinBind by editing “/etc/pam.d/sshd”. This will also do the automatic home directory creation.
2. Add “auth sufficient /usr/local/lib/pam_winbind.so # Allows access to everyone in the domain” to the 3rd line under “# auth”
3. Add “session required /usr/local/lib/pam_mkhomedir.so” to the 2nd line under “# session # Creates home directories for AD authenticated users.”
4. You can also run “getent passwd” and “getent group” to get the list of users and groups that combine both the domain controllers user list with the local list and the same for groups.
Testing Domain Authentication
1. Try logging into the account with an account on the domain controller and its password. Once logged in make sure the account has a home directory by typing “pwd” to see your current path.
Setup AD Group Access Restrictions
1. Now we need to restrict the FreeBSD box to particular users. We do not want everyone to have access. No now we will need to gather some needed information.
a. Run “wbinfo -g” to view all of the groups that are in the domain controller or look in the Active Directory Users and Computers.
b. Note the groups you want to have access to the box. You are required to add “Domain Admins” as a group to all FreeBSD boxes.
c. Next we need the SID of each of the groups.
i. wbinfo -n “GROUPNAME” , will return the SID of the group.
fbtest2# wbinfo -n “domain admins”
S-1-5-21-1328793019-4053271937-1264903302-512 Domain Group (2)
ii. The long number starting with S is the SID, i.e. S-1-5-21-1328793019-4053271937-1264903302-512
2. Now we need to add the SID’s to /etc/pam.d/sshd to allow those users access and to remove access for everyone.
a. Comment out “auth sufficient /usr/local/lib/pam_winbind.so # Allows access to everyone in the domain”
b. Add “auth sufficient /usr/local/lib/pam_winbind.so try_first_pass require_membership_of=
i.e. “auth sufficient /usr/local/lib/pam_winbind.so try_first_pass require_membership_of=S-1-5-21-1328793019-4053271937-1264903302-512 # Group: Domain Admins”
c. Make sure you label the “GROUP NAME” so that we know which group the SID belongs to.
d. Add the rest of the groups you want to have access to the box.
3. Add a user to a group on the domain controller and test your loggin.
Monday, August 11, 2008
The Largest Wifi Wireless Cracking in U.S
The US Department of Justice announced Tuesday that 11 people allegedly involved in the cracking of nine major U.S. retailers and the theft and sale of more than 40 million credit and debit card number have been charged. This is considered as the largest-ever identity theft case.
From the BBC news:
The 11 suspects are alleged to have obtained card numbers, account information and password details by driving around neighbourhoods and hacking into wireless equipment.
They are said to have then concealed the information in computer servers both in the US and Europe.
The Department of Justice said the scam caused "widespread" losses among banks, retailers and ordinary consumers - although it did not put a precise figure on the financial damage.
From the BBC news:
The 11 suspects are alleged to have obtained card numbers, account information and password details by driving around neighbourhoods and hacking into wireless equipment.
They are said to have then concealed the information in computer servers both in the US and Europe.
The Department of Justice said the scam caused "widespread" losses among banks, retailers and ordinary consumers - although it did not put a precise figure on the financial damage.
Qmail-ldap with SMTP Auth
Authenticated SMTP with SMTP-AUTH
SMTP AUTH is particulary useful when you have roaming users as well as users with dynamic IP assigned by their ISPs. These users can now use your SMTP server to relay their mails even if their IP or network is not listed in your allowed list of networks/IPs in qmail-smtpd.cdb file. Authenticated SMTP will allow such users to enter their credentials which are verified against their account entry in qmail-ldap and upon successful authentication they will be granted access to relay mails using your server regardless of their current IP or network. Read more about relaying in my mail relaying document.
In order to qmail-smtpd support this functionality you have to edit current /var/qmail/boot/qmail-smtpd/run script to invoke auth-smtp program installed with qmail-ldap in your installation. Open this file in your favorite editor and look for the following lines towards end of file.
exec \
envuidgid $QUSER \
tcpserver -v -URl $ME -x$QMAIL/control/qmail-smtpd.cdb \
${CONCURRENCY:+"-c$CONCURRENCY"} ${BACKLOG:+"-b$BACKLOG"} 0 smtp \
$PBSTOOL \
$QMAIL/bin/qmail-smtpd
Add command $QMAIL/bin/auth_smtp /usr/bin/true to the last line, so now the last line in your run script become..
exec \
envuidgid $QUSER \
tcpserver -v -URl $ME -x$QMAIL/control/qmail-smtpd.cdb \
${CONCURRENCY:+"-c$CONCURRENCY"} ${BACKLOG:+"-b$BACKLOG"} 0 smtp \
$PBSTOOL \
$QMAIL/bin/qmail-smtpd $QMAIL/bin/auth_smtp /usr/bin/true
Now add these variables to your qmail-smtpd.rules file
:allow,SMTPAUTH="AUTHREQUIRED",NOPBS=""
So now your qmail-smtpd.rules file will look as shown below
127.:allow,RELAYCLIENT=""
:allow,SMTPAUTH="AUTHREQUIRED",NOPBS=""
Now you have to rebuild the cdb file from qmail-smtpd.rules file. For this you have to issue following command as root. The variable SMTPAUTH tells qmail-smtpd that authorization is required before relaying mail from your server. Next variable NOPBS tells smtpd not to use PBS (POP Before SMTP). You do not need this since you are using SMTP AUTH. This may be required when you are using clustered servers but not now.
# tcprules qmail-smtpd.cdb rules.tmp < qmail-smtpd.rules
You have to restart the smtpd service for these changes to take effect. To do this issue following command as root.
# svc -t /service/smtpd
To test this setup try sending mail from some other host using sender's address on mail envelop as your servers default domain. It should ask you for authentication. If this works, you are done with SMTP AUTH. Don't forget to verify the service is running using svstat command as follows before you test.
# svstat /service/smtpd
/service/smtpd: up (pid 26698) 14 seconds
SMTP AUTH is particulary useful when you have roaming users as well as users with dynamic IP assigned by their ISPs. These users can now use your SMTP server to relay their mails even if their IP or network is not listed in your allowed list of networks/IPs in qmail-smtpd.cdb file. Authenticated SMTP will allow such users to enter their credentials which are verified against their account entry in qmail-ldap and upon successful authentication they will be granted access to relay mails using your server regardless of their current IP or network. Read more about relaying in my mail relaying document.
In order to qmail-smtpd support this functionality you have to edit current /var/qmail/boot/qmail-smtpd/run script to invoke auth-smtp program installed with qmail-ldap in your installation. Open this file in your favorite editor and look for the following lines towards end of file.
exec \
envuidgid $QUSER \
tcpserver -v -URl $ME -x$QMAIL/control/qmail-smtpd.cdb \
${CONCURRENCY:+"-c$CONCURRENCY"} ${BACKLOG:+"-b$BACKLOG"} 0 smtp \
$PBSTOOL \
$QMAIL/bin/qmail-smtpd
Add command $QMAIL/bin/auth_smtp /usr/bin/true to the last line, so now the last line in your run script become..
exec \
envuidgid $QUSER \
tcpserver -v -URl $ME -x$QMAIL/control/qmail-smtpd.cdb \
${CONCURRENCY:+"-c$CONCURRENCY"} ${BACKLOG:+"-b$BACKLOG"} 0 smtp \
$PBSTOOL \
$QMAIL/bin/qmail-smtpd $QMAIL/bin/auth_smtp /usr/bin/true
Now add these variables to your qmail-smtpd.rules file
:allow,SMTPAUTH="AUTHREQUIRED",NOPBS=""
So now your qmail-smtpd.rules file will look as shown below
127.:allow,RELAYCLIENT=""
:allow,SMTPAUTH="AUTHREQUIRED",NOPBS=""
Now you have to rebuild the cdb file from qmail-smtpd.rules file. For this you have to issue following command as root. The variable SMTPAUTH tells qmail-smtpd that authorization is required before relaying mail from your server. Next variable NOPBS tells smtpd not to use PBS (POP Before SMTP). You do not need this since you are using SMTP AUTH. This may be required when you are using clustered servers but not now.
# tcprules qmail-smtpd.cdb rules.tmp < qmail-smtpd.rules
You have to restart the smtpd service for these changes to take effect. To do this issue following command as root.
# svc -t /service/smtpd
To test this setup try sending mail from some other host using sender's address on mail envelop as your servers default domain. It should ask you for authentication. If this works, you are done with SMTP AUTH. Don't forget to verify the service is running using svstat command as follows before you test.
# svstat /service/smtpd
/service/smtpd: up (pid 26698) 14 seconds
Thursday, August 7, 2008
Few Googles search Tip & Tricks
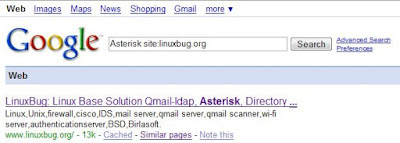
When it comes to the Google search box, you already know the tricks, but today i am going to show you few cool search tricks.
1.) Get local time anywhere
Type this key words on google search box what time is it USA
2.) Convert currency, metrics, bytes and more
Key words : 1 US dollars in indian money, 1 kilo in pounds, 85 f to c
3.) cache snapshot of your sites
Key words : cache:linuxbug.org
4.) Remove affiliate links from product searches
Key Words : satish -site:linuxbug.org
5.) Get Movie times anywher
Key Words : movie times
6.) Search specific type of files
Key Words : filetype:pdf
7.) Find key words on specified website
Key words : Asterisk site:linuxbug.org
8.) Find Music on google
Key words : -inurl:(htm|html|php) intitle:"index of" +"last modified" +"parent directory" +description +size +(wma|mp3) "shakira"
How to compile Linux Kernel
Compiling custom kernel has its own advantages and disadvantages.Compiling kernel needs to understand few things and then just type couple of commands. This step by step howto covers compiling Linux kernel version 2.6.xx under Debian GNU Linux.
Few step to compile kernel.
# cd /usr/src
# wget http://www.kernel.org/pub/linux/kernel/v2.6/linux-x.y.z.tar.bz2
Notes : Make sure GCC and GNU make utility installed on your system before compile kernel.
# tar cvjf linux-x.y.z.tar.bz2
# cd linux-x.y.z
Compile kernel
# make menuconfig
Start compiling to create a compressed kernel image, enter:
# make
compiling to kernel modules
# make modules
Install kernel modules
# make modules_install
To install kernel
# make install
It will install three files into /boot directory as well as modification to your kernel grub configuration file
System.map-2.6.25
config-2.6.25
vmlinuz-2.6.25
Create an initrd image for new installed kernel
# cd /boot
# mkinitrd -o initrd.img-2.6.25 2.6.25
Modify Grub configuration file - /boot/grub/menu.lst
# vi /boot/grub/menu.lst
title Debian GNU/Linux, kernel 2.6.25 Default
root (hd0,0)
kernel /boot/vmlinuz root=/dev/hdb1 ro
initrd /boot/initrd.img-2.6.25
savedefault
boot
Note: its hard to edit this file without knowledge of options so better way is use update-grub command it will do it automaticaly for you.
# update-grub
Now time comes up for testing reboot your system and boot with new kernel and enjoy your system. Good Bye
Few step to compile kernel.
# cd /usr/src
# wget http://www.kernel.org/pub/linux/kernel/v2.6/linux-x.y.z.tar.bz2
Notes : Make sure GCC and GNU make utility installed on your system before compile kernel.
# tar cvjf linux-x.y.z.tar.bz2
# cd linux-x.y.z
Compile kernel
# make menuconfig
Start compiling to create a compressed kernel image, enter:
# make
compiling to kernel modules
# make modules
Install kernel modules
# make modules_install
To install kernel
# make install
It will install three files into /boot directory as well as modification to your kernel grub configuration file
System.map-2.6.25
config-2.6.25
vmlinuz-2.6.25
Create an initrd image for new installed kernel
# cd /boot
# mkinitrd -o initrd.img-2.6.25 2.6.25
Modify Grub configuration file - /boot/grub/menu.lst
# vi /boot/grub/menu.lst
title Debian GNU/Linux, kernel 2.6.25 Default
root (hd0,0)
kernel /boot/vmlinuz root=/dev/hdb1 ro
initrd /boot/initrd.img-2.6.25
savedefault
boot
Note: its hard to edit this file without knowledge of options so better way is use update-grub command it will do it automaticaly for you.
# update-grub
Now time comes up for testing reboot your system and boot with new kernel and enjoy your system. Good Bye
BlackTrack
OpenSER Integration with Asterisk
Let's talk about something interesting. I have been working on IP telephony systems for the last year. I have implemented IP PBX solutions for many organizations. I have good expertise on telephony and Asterisk systems. Basically Asterisk is not a SIP server but it can support the SIP protocol. That's why Asterisk can handle only 200 to 300 SIP device registrations, and that on large productions it doesn't to work great. Finally, I have decided to implement Asterisk on a large production with the help of OpenSER. OpenSER is pure SIP server and a lightweight binary, so it can handle 10,000 call per second. I am using OpenSER in front of Asterisk. OpenSER handles my call SIP registration requests, and Asterisk handles my PSTN functionality because OpenSER doesn't support telephony hardware. Asterisk provides media application services like VoiceMail, Conference, IVR, and PSTN functions.
I am going to show you how to integrate this combined system: OpenSER and Asterisk.
OpenSER Integration with Asterisk
I am going to show you how to integrate this combined system: OpenSER and Asterisk.
OpenSER Integration with Asterisk
OpenWRT
The OpenWrt project will over the next two months focus on a new Kamikaze release. The official name is to be: OpenWrt Kamikaze 8.08 Release. The planned schedule will take the following shape:
*Last day in July - final release candidate: 8.08 RC-1. This will be a feature freeze, and all changes after this point will be bug fixes.
*Last day in August - final release: OpenWrt Kamikaze 8.08 Release.
OpenWrt Kamikaze 8.08 Release will, amongst other, focus on bringing the following features:
- Firewall rewrite
- Broadcom 47xx running reliably with the new Kernel, not including wifi
- IMQ and Traffic shaping tested with newer kernels, especially 2.6.25
- Sysupgrade for more platforms (x86 is tested again)
- The new web interface (LuCI, Lua Configuration Interface)
- Full support for new platforms and targets
- Attention towards the integration of security updates
- Package maintaining and updates between releases
The OpenWrt Team
*Last day in July - final release candidate: 8.08 RC-1. This will be a feature freeze, and all changes after this point will be bug fixes.
*Last day in August - final release: OpenWrt Kamikaze 8.08 Release.
OpenWrt Kamikaze 8.08 Release will, amongst other, focus on bringing the following features:
- Firewall rewrite
- Broadcom 47xx running reliably with the new Kernel, not including wifi
- IMQ and Traffic shaping tested with newer kernels, especially 2.6.25
- Sysupgrade for more platforms (x86 is tested again)
- The new web interface (LuCI, Lua Configuration Interface)
- Full support for new platforms and targets
- Attention towards the integration of security updates
- Package maintaining and updates between releases
The OpenWrt Team
FreeBSD 7.0-RELEASE
Subscribe to:
Posts (Atom)

